PULSE – Agile Red Team Engagement
 Introduction
Introduction
PULSE is a Prism Infosec Agile Red Team service. It is a stepping stone for organisations who are not yet ready for a full Red Team engagement but want to understand their security posture and evaluate their defences against real world threats.
Why Pulse?
Red Teaming is a fantastic tool for exercising security tooling, staff, policies, and procedures in a realistic, secure, and safe manner. It does this by taking the Tactics, Techniques and Procedures of genuine cyber threat actors and applies them in intelligence led scenarios which can span multiple weeks. However, not every organisation is ready for the cost, time, and effort that a full red team engagement requires to deliver value for the business.
Penetration Tests are great services for contained evaluations of the security boundaries and controls of distinct systems. It excels at analysis of specific vulnerabilities contained to specific control planes of individual systems but struggles to deliver real-world tests of threat actor activities and capabilities.
Pulse seeks to bridge the gap between costly Red Teams and contained Penetration Test. It does this by focusing on the scenario of an opportunistic cyber threat actor seeking to breach the perimeter, establish a foothold, and compromise the environment in the space of a working week. We compress a Red Team scenario into this timeframe by unit testing specific phases of breach in a controlled manner which does not risk disrupting ongoing work but still effectively exercises the security controls in a declared manner.
Key Features of PULSE
- PULSE is best suited for organisations who have invested in security tooling but lack a full-time dedicated Security Operations Centre and staff.
- A unit testing approach means that testing can be flexible, repeatable, and measurable.
- Over a 5-day testing phase it seeks to evaluate the security of an organisation’s perimeter, endpoint security, and environment, from the point of view of a time limited, opportunistic, threat actor.
- The service uses techniques linked back to ATT&CK MITRE IDs so that you can clearly identify what real-world Tactics, Techniques, and Procedures have been exercised.
PULSE Methodology
PULSE has a modular methodology which does follow traditional breach attack paths. It is able to move at pace by sacrificing stealth for a smash and grab approach, rapidly testing multiple different payloads and delivery mechanisms in a manner similar to a purple team but combining that a red team evaluation of environment to determine how an opportunistic threat actor could use an established foothold to impact an organisation.
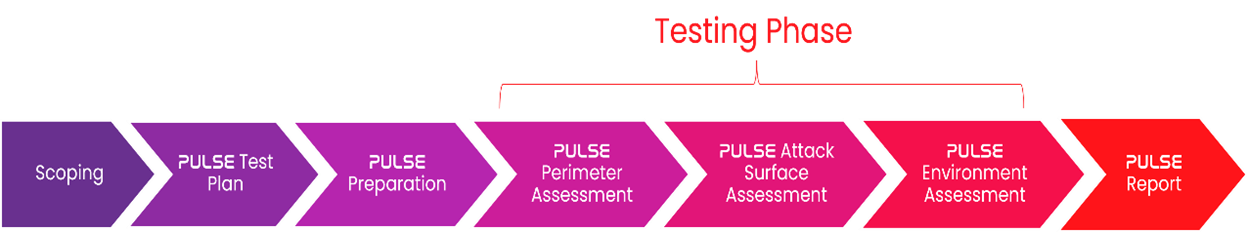
To deliver this effectively, we break a PULSE engagement into the following steps:
- Scoping – Following a Pre-Sales discussion with your account manager, a scoping call will be held with one Prism Infosec’s experienced Red Team consultants to capture the information needed for a successful engagement.
- PULSE Test Plan – The consultant will put together a tailored test plan based on the PULSE methodology, and the details from the scoping questionnaire.
- PULSE Preparation – Clients will provide the pre-requisites whilst Prism Infosec’s consultant prepares payloads, infrastructure, and tooling.
- PULSE Perimeter Assessment – Testing begins with an assessment of the perimeter – different payload delivery techniques are sent in to see what gets through.
- PULSE Attack Surface Assessment – For payloads which get through the perimeter we then assess which ones would succeed against the installed security products. Working with your staff, we assess which ones alert, which ones are blocked, and which ones succeed.
- PULSE Environment Assessment – Using a successful payload, we then assess your environment. Investigating how far a threat actor can get within a week.
- PULSE Report – the outcomes of all three phases are then documented, along with recommendations to harden your environment, and suggestions and advice for follow-up testing to improve your security posture.
What about physical testing?
Thanks to the modular nature of PULSE, should a client want to include a physical test element, we can customise the service to include a short physical testing phase. During this one of our consultants will spend a day evaluating the physical controls of an organisation’s location before trying to physically breach the perimeter using a variety of real-world social engineering and physical breach techniques before attempting to achieving a specified objective. This approach is covered by our risk management strategy, during which we will guide clients through the art of the possible to ensure a safe, legal, and effective test can be conducted.
Risk Management
Real world threats do not target non-production systems, and organisations will only really be able to defend themselves properly if testing occurs on those same production environments. Testing in Production however carries significant risks to business disruption.
We recognise this, and as with all of Prism Infosec’s Red Team services, we have applied our risk management strategy that seeks to minimise the chance of disruption, permits realistic testing, and ensures that client control is supported by expert knowledge.
The PULSE risk management strategy is documented and provided in the test plan; this is reviewed with clients prior to preparation and is enforced during testing.
Deliverables
The service deliverable shall be a technical report clearly documenting the outcomes of each phase of testing, combined with a short narrative of the environment testing, alongside practical, pragmatic, clear and concise recommendations on how to improve the security posture of the organisation.
Email Prism Infosec, complete our Contact Us form or call us on 01242 652100 and ask for Sales to setup an initial discussion.