Latest news
Passwords
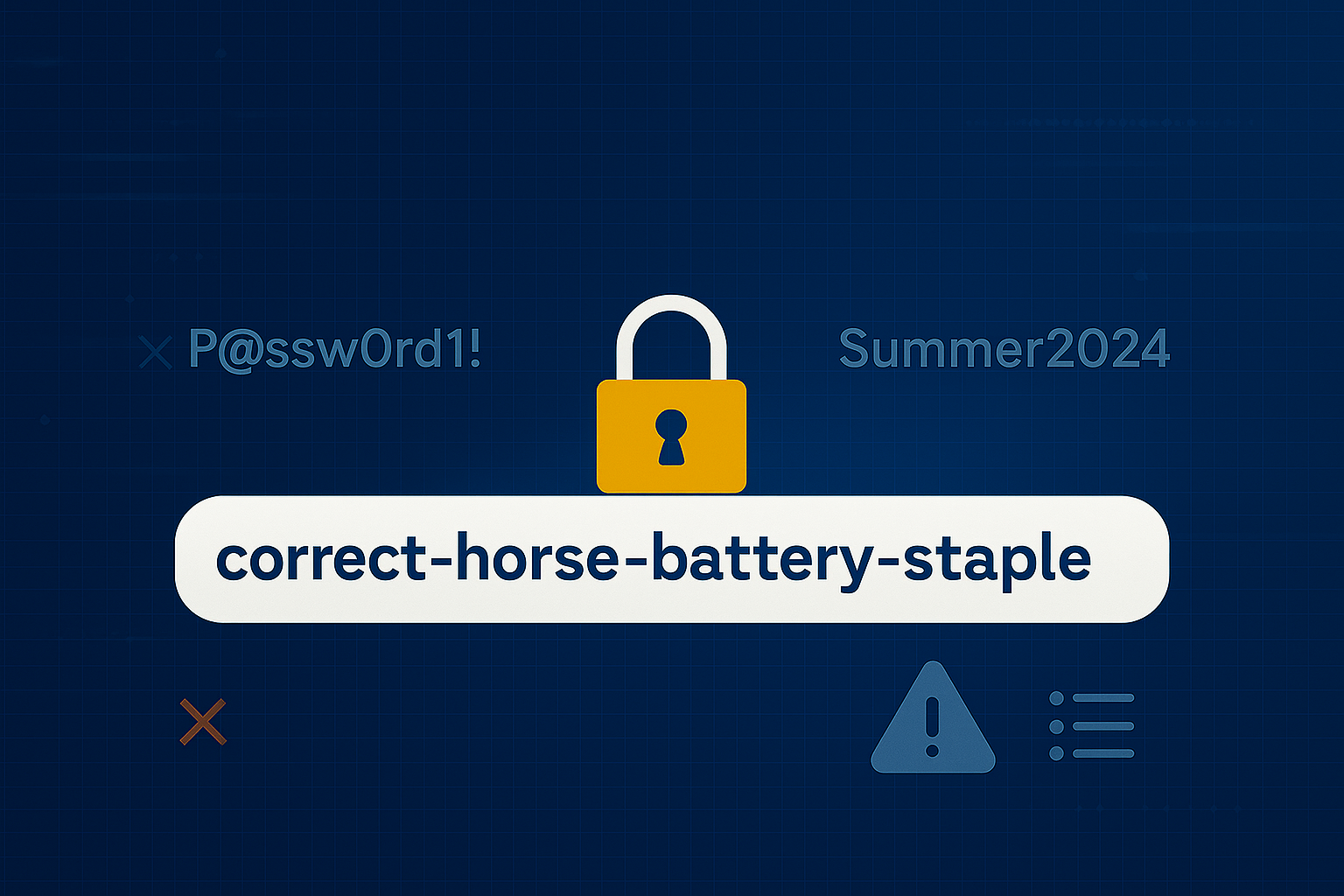
NIST, like the NCSC have updated their password guidance. It is now no longer advisable to set them to be random strings of nonsensical letters, numbers and symbols. The focus is now on password length, by stringing together multiple words. Inclusion of uppercase, and symbols or numbers is still helpful, to make them even harder for threat actors to guess. It is also no longer advisable to rotate passwords frequently – instead, passwords should be checked against known bad lists and breaches should be monitored. If the password is identified in those lists, or an incident occurs with the associated account, then it should be rotated.
Frankly it’s about time these caught up with the realities of the real world. Users will often choose weak but easy to remember passwords, and deliberately craft them to match password complexity rules. Often these will be incremented by a digit when a forced expiry occurs. This makes them extremely weak and vulnerable – especially once the pattern is identified!
At Prism Infosec we often don’t need to breach systems with fancy exploits due to poor credential management practices. We often get asked to help clients conduct credential audits by performing cracking exercises and testing against known bad lists to support them whilst they are updating their internal guidance and strategy.
Updated guidance: