Latest news
Cyber Threats & The Boardroom
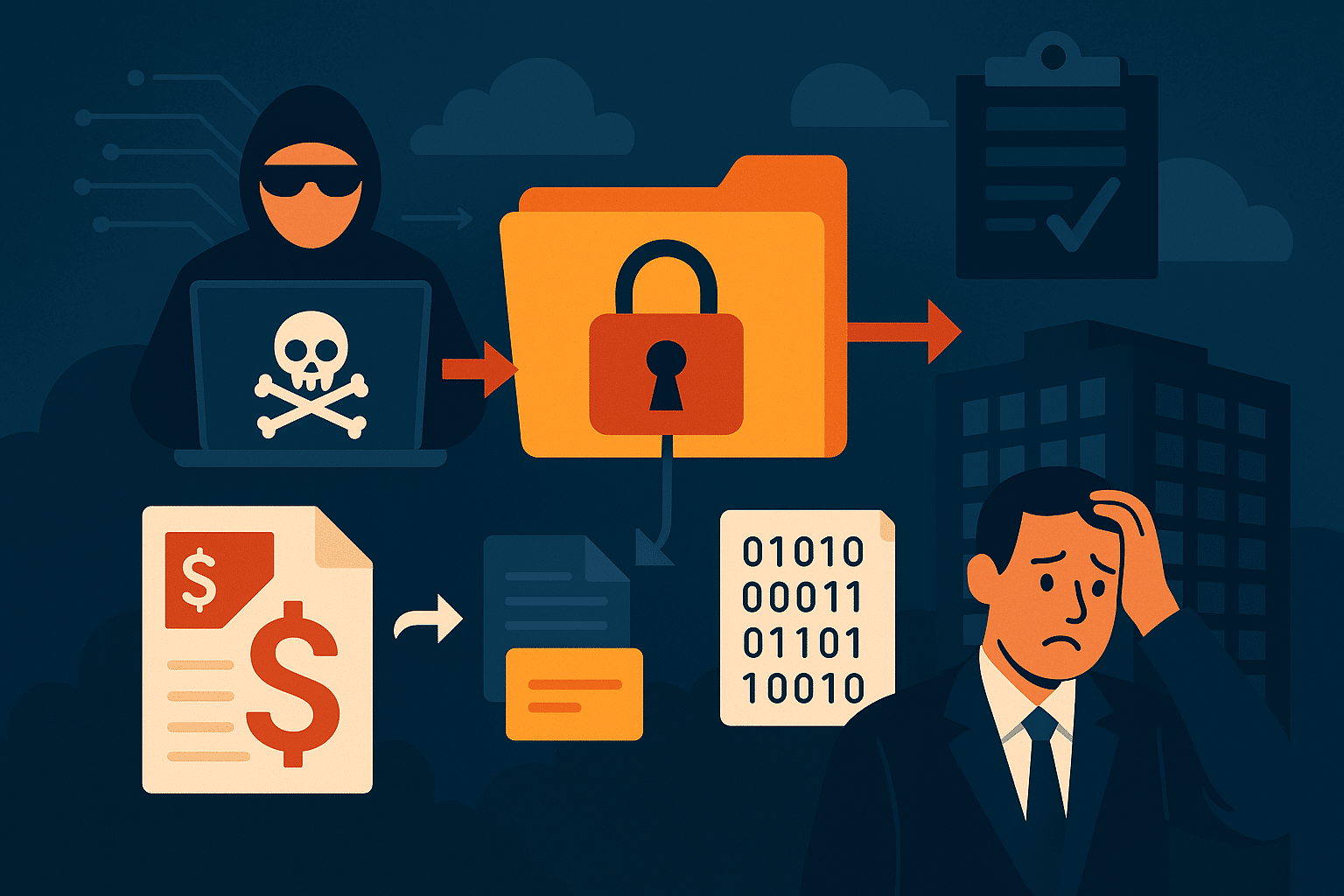
In cybersecurity, the prevalent and growing threat from criminals is ransomware operations. This is where a threat actor manages to establish a foothold into an organisation, will try to position themselves to gain control of the organisation’s data, will often steal some or all of that data, and then encrypt as much of it as they can. They will then contact the organisation and demand payment to restore that data, often they will also use the stolen data they have in their possession to prove their access, and use it to blackmail the organisation into paying, or sell it on to other threat actors. Regardless of the outcome, the impact to the organisation is usually severe with losses to share price, customer confidence, massive operating cost increases, and additional supply chain knock on effects. These attacks have crippled many organisations and the number of attacks continues to grow. They cannot be treated as purely an IT department issue and often sit as a risk with the board.
The UK and the EU have started to take steps to raise the priority of defending against these sorts of issues through DORA (the EU Digital Operational Resilience Act) and the CSR (the UK’s Cyber Security and Resilience Bill). These empower regulators and appropriate bodies to take action against firms that fail to address specific threats, sometimes with significant fines. Whilst many organisations do invest in security systems, they have insurance, and they even sometimes have third party incident response retainers, properly exercising those systems is often seen as too costly and too impactful for the business. This is unfortunately short-term thinking, as most organisations have no idea how effective these systems actually are until they are tested under fire and fully utilised to determine if what is down on paper, will match reality should the worst happen. It’s a bit like installing a fire alarm in a house but never actually testing it to see if it works, and instead just hoping it will if a fire breaks out.
In Red Teaming simulations, companies like Prism Infosec will often assume the role of these real world threat actors to help an organisation understand how vulnerable they are to these sorts of attacks, and to help them exercise their incident and response systems. This gives an organisation the ability to understand how staff and their systems react if a threat actor manages to gain a foothold.
These simulations however are only effective when the executive body of an organisation engage with them to understand the identified risks, and put emphasis on addressing them.