In cybersecurity, red teams and incident responders often work on different stages of the same challenge — understanding malicious artefacts, analysing payloads, and reporting findings safely and accurately. To support these workflows, we built PRIMAL.
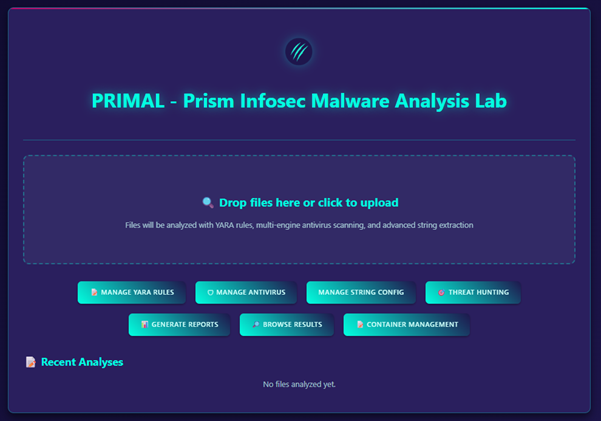
Originally developed for our red team, PRIMAL helps us signature custom implants, run static scans before deployment, and document tool footprints for post-engagement reporting — ensuring we can confidently distinguish what was ours and what wasn’t. Over time, we adapted PRIMAL to strengthen our incident response services, where efficient and controlled analysis is critical.
What PRIMAL Does
PRIMAL is a static malware analysis toolkit designed to support both offensive and defensive security operations. Key features include:
- Dockerised ClamAV and YARA scanning
- Entropy calculations and basic file analysis
- Custom string searches for sensitive indicators
- Generation of IOCs, YARA rules, and KQL queries
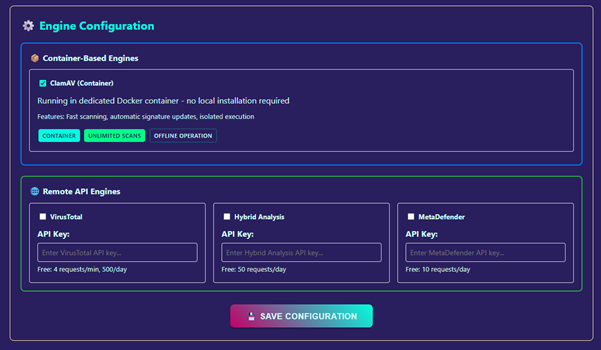
- Optional submissions to MetaDefender, VirusTotal, and Hybrid Analysis (API keys required)
- Modular architecture, allowing future integration of additional AV engines and analysis tools
- Easy deployment: can run on a segregated VM for live investigations or in a cloud environment thanks to its containerised build
Why Strings, Entropy, AV and YARA Matter
When developing custom payloads for red team engagements or triaging artefacts during incident response, understanding what’s inside a file before it’s deployed or reported is essential. PRIMAL provides several layers of insight:
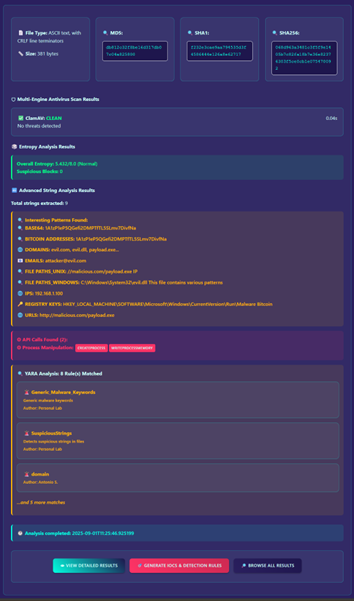
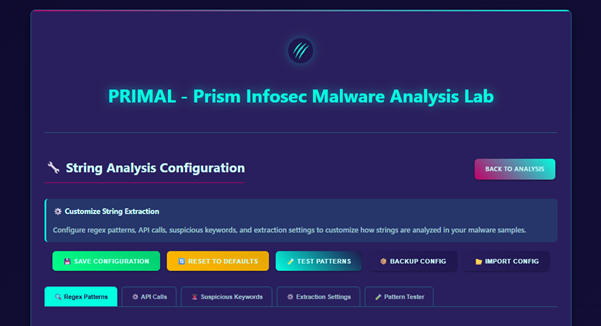
String Analysis
Red teams often need to search payloads for sensitive strings to avoid accidentally exposing operations or alerting defenders prematurely. Examples include:
- Client names or project identifiers unintentionally compiled into binaries
- Red team company names or internal codenames that could reveal testing activity
- Development environment references that might link payloads back to internal tooling
- Fallback C2 URLs that should remain undiscovered until needed
By identifying these strings early, we ensure payloads remain clean, safe, and operationally secure.
Entropy Analysis
Entropy measures how “random” the data within a file appears:
- High entropy often suggests packed, encrypted, or obfuscated code
- Low entropy can expose readable strings or identifiable signatures
For red teams, this helps fine-tune payloads to minimise unnecessary detection. For incident responders, entropy analysis provides fast insights into whether a suspicious file may be malware, packer-protected, or benign — speeding up investigations.
Antivirus (AV) Scanning
Although PRIMAL focuses on static analysis only, scanning payloads against Dockerised ClamAV offers a valuable quick check for:
- Unintentional detection of red team tools prior to deployment
- Third-party library fingerprints that may be flagged by AV engines
- Early visibility into signatures already known to defenders
For incident responders, AV results provide a first-pass triage to determine whether a file is already recognised as malicious.
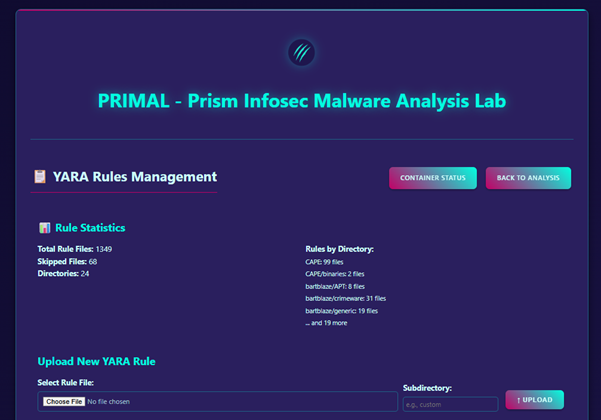
YARA Rules
YARA is a powerful pattern-matching framework used widely in both offensive and defensive contexts:
- For red teams, YARA ensures our custom implants and payloads aren’t inadvertently detected based on existing signatures.
- For incident responders, YARA accelerates threat hunting by enabling the creation of bespoke rules to locate similar artefacts across an environment.
PRIMAL integrates YARA in both directions: scanning files against known rules and generating new YARA signatures to support proactive detection.
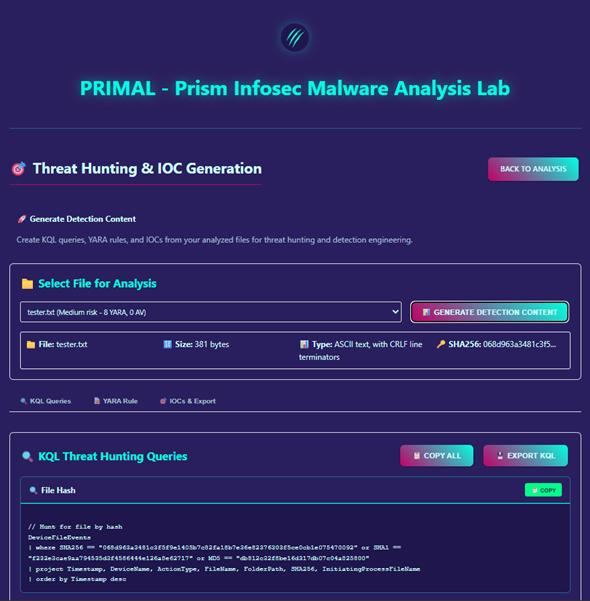
Threat Hunting Capabilities
PRIMAL goes beyond analysis by supporting threat hunting workflows directly. For every file it processes, the tool can generate:
- Indicators of Compromise (IOCs)
- Custom YARA rules
- KQL queries suitable for querying Microsoft Sentinel or other SIEM systems
These outputs allow incident responders and security teams to:
- Quickly identify similar artefacts across endpoints and logs
- Build proactive detection rules before a threat spreads
- Reduce the time between initial detection and containment
For red teams, generating these outputs also allows testing and validating detections, helping teams understand which artefacts might trigger alerts in real-world scenarios.
Easy Deployment
PRIMAL has been designed with deployment flexibility in mind:
- Run on a segregated VM to safely analyse artefacts during live investigations
- Deploy in a cloud environment thanks to its containerised architecture
- Minimal setup required — start analysing immediately without complex configuration
This makes PRIMAL suitable for a wide range of operational scenarios while keeping analysis isolated and secure.
Built for Control and Accountability
PRIMAL was designed to operate in controlled environments — ensuring payloads are analysed safely, maintaining full transparency, and supporting the trust we build with our clients.
An Experiment in AI-Assisted Development
PRIMAL was also an experiment in leveraging Claude.ai during its development. We wanted to explore how large language models could assist in building supporting tools that strengthen the wider cybersecurity community. While PRIMAL was designed, tested, and validated by our engineers, experimenting with AI allowed us to accelerate parts of the process and explore innovative approaches to tool-building.
Open Source and Available Now
We’re pleased to make PRIMAL available to the wider cybersecurity community.
🔗 Get it here: https://github.com/PrismInfosecLabs/PRIMAL/tree/release
Whether you’re simulating adversaries or responding to incidents, PRIMAL helps you analyse artefacts, generate detections, and improve security outcomes.

















